eFlow Security Hub
Online Fraud and Security
Fraud and scams are becoming more common, and more sophisticated. Scammers are targeting people nationwide with fraudulent texts claiming to be from eFlow.
The eFlow Security Hub aims to create awareness of scam attempts and educate our customers to be more scam savvy.
eFlow does not send text messages with links to customers.
Scam Examples
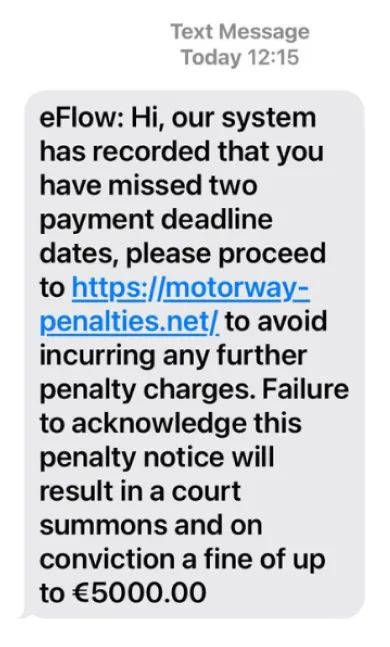
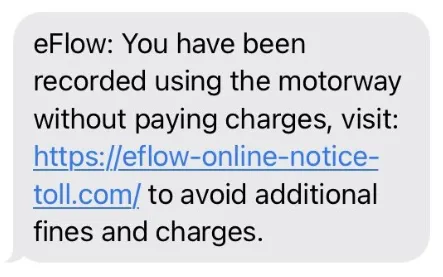
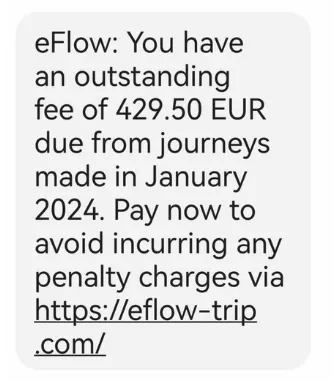
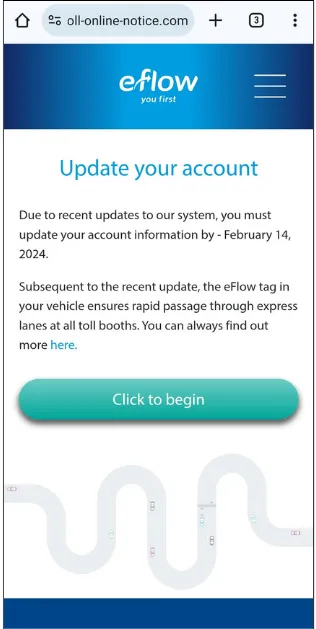
Fraudsters are sending text messages to people nationwide claiming to be from eFlow. These messages usually express a tone of urgency, asking the receiver to click on a link and take an immediate action.
Typical actions include paying a toll or accepting new terms and conditions. eFlow does not send links in text messages. If you receive one, delete it immediately. The eFlow system has not been compromised or subjected to a data breach.
Below are some examples of the most common scam messages we’ve seen and fraud websites created by scammers:
Phone Fraud
Phone fraud is one of the most common ways scammers target potential victims by contacting you by phone text claiming to be from a reputable organisation such as a bank, service provider or government body. During the conversation or text message, the scammer will look for personal, financial or security information to make a financial transaction.
The communication will typically come with a sense of urgency asking you to “verify”, “update”, “reactivate”, their account. Scams often indicate a payment failure or toll to be paid, calling for immediate action. Scammers will give you little time to reason or question the legitimacy of the question.
Some scam texts may include a link which will download malicious software to your device once clicked. The scammer will use the information gathered to steal money from your bank account.
While current scams are focused on text messages, a scammer may also call you claiming to be from eFlow informing you of an unpaid toll, penalties related to a toll journey, expired payment details or account suspension. eFlow will never directly contact you via phone call or text to confirm or update personal information.
If you receive a suspicious link, please report the exact website name by email to scam@netcraft.com or on the web to https://report.netcraft.com.
Netcraft is a cybersecurity company that provides internet security services and help organisations and individuals protect against online threats, malware, and other cybersecurity issues.
To become more aware and savvy to scams remember the below tips:
- Be wary of unsolicited phone calls or voicemails.
- Never provide personal information unless you have confirmed the speaker is an official representative from the organisation by:
a) Take the caller’s number and tell them you will call them back once the number has been verified.
b) Look up the organisations phone number and validate it.
c) Do not call the number provided as it could be fake.
d) If the caller is genuine they will understand and await your reply. - Don’t respond to texts seeking financial information.
- Fraudsters may have personal information about you (name, address, Eircode) to trick you into believing they are legitimate. Do not assume they are genuine because they have these details.
- You can independently check the caller’s identity by calling the number on another phone line.
- eFlow will never ask you for personal information or payment details via text or phone call.
Stay safe and think before you click!
Scam Dictionary
Scammers use a variety of techniques to trick people into handing over personal information to gain access to their personal finances. The terminology around this type of fraud is constantly changing. Below is a list of fraud and security terms you should be familiar with.
Antivirus
Software created to detect, prevent, and eliminate viruses and other forms of malicious software, helping people avoid falling victim to scams.
Cyber-attack
Malicious endeavours aimed at harming, disrupting, computer systems, networks, or devices through cyber means.
Cybersecurity
The safeguarding of devices, services, and networks, along with the protection of the information they contain, against theft or damage.
Data hack
Also known as a data breach or data security breach, refers to the unauthorised access, acquisition, or disclosure of personal information stored in a computer system, network, or database. It involves the intentional or unintentional intrusion into a system's security measures by hackers or cybercriminals, resulting in the compromise of personal, financial, or other sensitive data.
Malware
Malware is any program or file designed with the explicit purpose of causing harm to a computer, network, or server. There are various forms of malware, including computer viruses, worms, Trojan horses, ransomware, and spyware. These harmful programs engage in activities such as stealing, encrypting, or deleting sensitive data; manipulating or taking control of critical computing operations; and monitoring the activities of computer users.
Multi-factor authentication
An authentication method that asks users to provide two or more verification factors to access their account such as entering a six code sent to your mobile or email to confirm you are logging in.
Phishing
Mass emails sent to numerous individuals without targeting them specifically, requesting sensitive information (such as bank details) or enticing them to visit counterfeit websites.
Pharming
When scammers use malicious software to redirect you to their scam website despite entering the correct site you wanted to visit.
Smishing
An SMS that looks like it was received from a bank or legitimate organisation, asking users to click on a fraudulent link to disclose personal information.
Ransomware
A malicious computer program that disables your computer and demands a fee to fix the issue.
Trojan Horse
Malicious software hidden within seemingly harmless data and looks like a normal program. When activated, the software can access information on your hard drive and send personal data to hackers.
Vishing
The deceptive practice of making phone calls or leaving voice messages impersonating reputable companies, with the intention of coaxing individuals into disclosing personal information such as bank details and credit card numbers.
Virus
Programs that possess the ability to self-replicate and are designed to infect legitimate software programs or systems. They fall under the category of malware.
Email Fraud
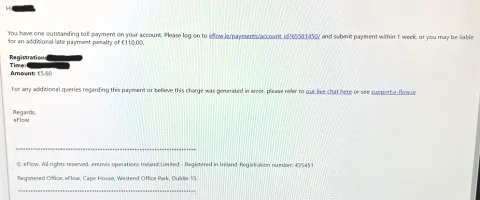
Fraud and scams remain prevalent, with scammers continuing to target road users to access personal and financial details. eFlow are aware of suspicious emails prompting customers to pay outstanding tolls and fines. eFlow will not send you any links for payment by email.
We understand an email about a toll payment can cause you worry. If you have not contacted eFlow recently and receive an email from us, remember to Stop, Ask, and Confirm the email is from eFlow. We’ve included some tips below to help watch out for scams.
Stop
If you receive an email with a link from eFlow, before acting make sure you:
- Take a few moments to fully read the email.
- Don’t click on any links.
- Check if you have contacted eFlow recently.
Ask
An email scam will prompt you to act by mentioning penalties, unpaid tolls and changes to your account. If you receive an unsolicited email from eFlow make sure to ask yourself:
- Have I contacted eFlow recently?
- Are the details correct (e.g. my vehicle, journey details, account details)?
- Did I recently drive through the M50 toll?
- Is the link from eflow.ie?
- Does the sender email address look legitimate?
Confirm
If you think you have received a suspicious email, we recommend:
- Logging into your eFlow account at eflow.ie to confirm all details are correct i.e. your vehicle, journey, and account details.
- If you don’t have an eFlow account, please contact us on one of our communication channels here to verify if the email is legitimate.
Remember to stay scam aware and to Stop, Ask, and Confirm if it’s legitimate. Please see an example below of a fraudulent email in circulation.
How to Recognise Scams
As scams are more prevalent than ever it can be difficult to distinguish fraudulent messages from genuine ones. We’ve compiled a list of best practices when identifying scams so you can become more scam aware.
- Be cautious of unsolicited messages: If you receive an unexpected SMS or email from an unknown sender or a sender you don’t typically interact with, exercise caution.
Verify the sender’s identity: Carefully inspect the sender’s email address to check the domain or texts received from an unknown phone number. Scammers often use email addresses or phone numbers that are slightly altered to mimic legitimate ones. Look for any inconsistencies or suspicious variations.
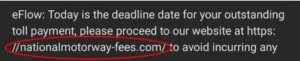
Beware of urgent requests: Scammers often create a sense of urgency to pressure you into taking immediate action without carefully considering the situation. Be cautious of messages that demand urgent responses or threaten negative consequences if you don’t comply.
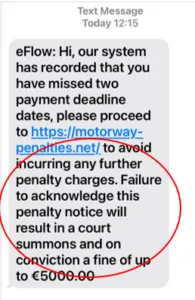
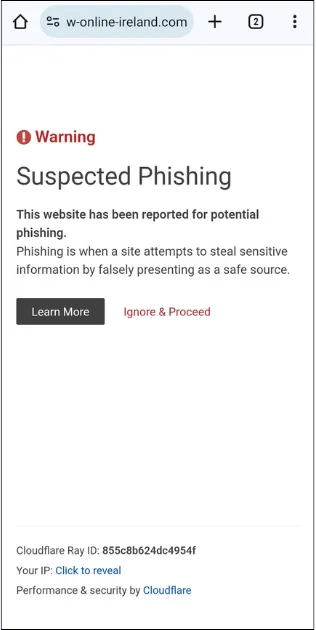
- Pay attention to suspicious URLs: Hover your mouse cursor over links in emails to view the actual destination URL before clicking. Ensure the URL matches the expected website or organisation. Be cautious of shortened URLs or URLs that appear unusual or unfamiliar. If you notice a suspicious URL report the exact website name by email to scam@netcraft.com or on the web to https://report.netcraft.com.
Netcraft is a cybersecurity company that provides internet security services and help organisations and individuals protect against online threats, malware, and other cybersecurity issues.
- Be sceptical of requests for personal information: Legitimate organisations generally don’t ask for personal or financial information through unsolicited messages. Be wary of messages requesting sensitive details like passwords, PPS number, or bank details.
- Look for official branding and contact information: Legitimate messages from reputable companies often include consistent branding, company logos, and accurate contact information. If something seems off or inconsistent, it could be a sign of a scam.
- Trust your instincts: If something feels off or too good to be true, trust your gut. Scammers often use tactics to exploit emotions, curiosity, or financial incentives.
- Stay updated on common scams: Stay informed about prevalent scam techniques and tactics. Regularly educate yourself about the latest scams in your region and be aware of common red flags to watch out for. See the most common eFlow scam text messages here.
- Tell your friends and family: It’s not just important to protect yourself but also help others. You can share these tips with your friends and family so the message can reach more people.
Most Popular Help Topics
- Ask customers to open links to confirm payment details.
- Send an SMS about a failed payment or outstanding penalties.
- Ask customers for payment information by clicking a link.
- Scammers have created professional-looking fake websites that imitate eFlow’s website.
- Messages typically direct recipients to follow a link to where the urgent action is directed to be taken.
- Scam messages can be received by anyone, including eFlow customers.
- If you received a text claiming to be from eFlow with a link, do not click it. Report the exact website name by email to scam@netcraft.com or on the web to https://report.netcraft.com.
- If you clicked on a suspicious link, please contact your bank immediately.
- Always pay outstanding toll amounts directly on our website, by calling our customer service team or at any Payzone retail outlet.
- Be cautious of unsolicited messages. Scammers often use such messages to obtain personal information.
- If something seems suspicious, it probably is. Always err on the side of caution and seek advice by contacting us if you’re unsure.
- Verify the identity of the sender. Scammers often impersonate legitimate businesses. Carefully inspect the sender’s email address to check the domain or texts received from an unknown phone number.
eFlow are aware of suspicious emails prompting customers to pay outstanding tolls and fines. If you receive such emails, please:
- Verify if the sender is from an eflow.ie email domain.
- Don’t click any links.
- Check if you contacted eFlow recently.
- Contact us using one of our communication channels here, to verify the email.
Make sure to Stop, Ask, and Confirm if the email is legitimate.
- Smishing is a combination of the words SMS and phishing. It is the fraudulent practice of sending text messages pretending to be from reputable companies in an attempt to retrieve individuals’ personal information, such as passwords or credit card numbers.
- The text messages claim to come from a trustworthy source such as your bank, a service provider like eFlow, or a government body.
- They are difficult to spot as they are written in the style of the organisation and can appear within a thread of messages received from the organisation.
eFlow does not send text messages with links to customers.
Below are some examples of the most common scam messages we’ve seen and fraud websites created by scammers:

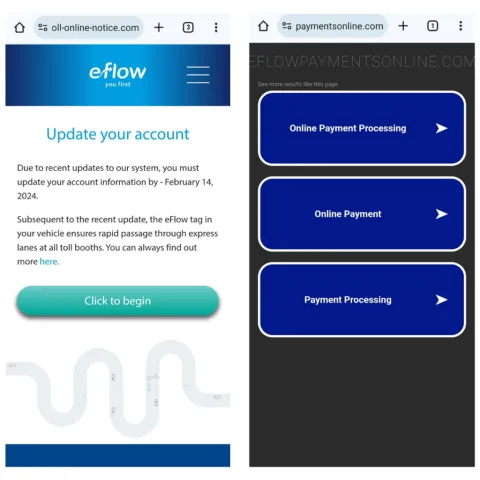
If you received a text claiming to be from eFlow with a link, do not click it, report the exact website name by email to scam@netcraft.com or on the web to https://report.netcraft.com.
Netcraft is a cybersecurity company that provides internet security services and help organisations and individuals protect against online threats, malware, and other cybersecurity issues.